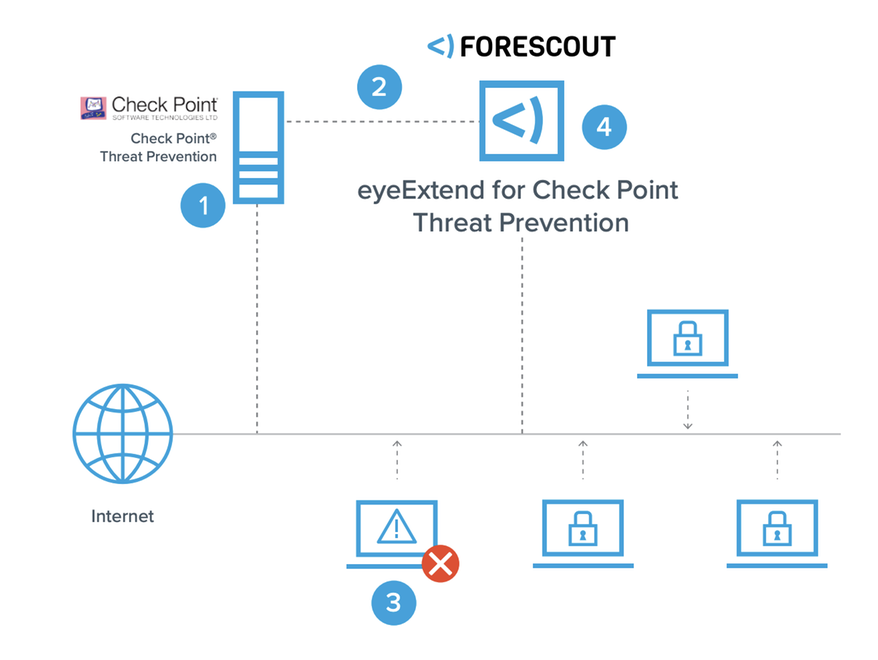
eyeExtend for Check Point® Threat Prevention
Strengthen advanced threat detection and accelerate threat response
- Developer
- Forescout
Eliminate threats from infected devices by killing suspicious processes
Forescout eyeExtend for Check Point Threat Prevention enhances the power of Check Point’s solution by helping organizations identify their entire attack surface, extend threat hunting to managed and unmanaged devices, and accelerate threat response
Features and Benefits
Leverage shared threat intelligence to maximize joint threat hunting and detection
When Checkpoint Threat Prevention identifies malicious files and IOCs on managed devices, it immediately notifies Forescout
eyeExtend for Check Point Threat Prevention. Forescout eyeExtend then extends this threat intelligence to the entire network using
Forescout platform, monitoring all network-connected devices—including unmanaged BYOD, guest and IoT devices—for IOCs.
The Forescout platform also uses the threat information provided by Check Point Threat Prevention to scan newer or transiently
connected devices for threat IOC’s the moment they connect. It then initiates device isolation and remediation, preventing the
spread of threats from any connected device across the network.Accelerate and automate policy-driven threat response
Forescout eyeExtend helps organizations react in real time to threats based on predefined security policies using Forescout
platform. IT and security teams can create Forescout policies for handling antibot, antivirus and threat emulation detections.
Based on policy and threat severity, the Forescout platform automatically takes appropriate actions such as restricting, isolating
or blocking compromised devices and initiating remediation workflows. These actions reduce mean time to respond and limit the
impact of threats.

Scan all Network Devices
Scan all network devices for
IOCs discovered by Check
Point Threat Prevention
Contain Threats
Contain threats by limiting or
blocking access of infected
devices to the network in
real time
Eliminate Threats
Eliminate threats from
infected devices by killing
suspicious processes
Notify Stakeholders
Notify stakeholders such as
security teams via emails
detailing specific threats
and their affected devices
Out-of-the box Integrations
Get out-of-the-box
integration with Check
Point Anti-Bot Software
Blade, Anti-Virus Software
Blade and SandBlast
Threat Emulation for easy
deployment and a quick ROI
Additional Information
Support
EyeExtend modules are fully supported by Forescout. Please see support details at https://www.forescout.com/resources/activecare-maintenance-and-support-policy/
- Phone: +1-866-377-8773
- Knowledge Base
- Read Documentation
Categories
-
App Type
-
Built By
-
Licensing Category
-
Works With
Resources
Forescout eyeExtend for Check Point® Threat Prevention Data Sheet
Download PDF