eyeExtend for Splunk®
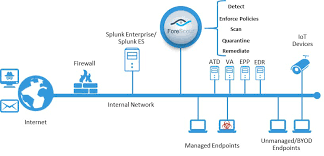
Capitalize on Forescout's rich contextual information
- Developer
- Forescout
Effectively Reduce Risk
Your cyber attack surface consists of all connected devices accessing your network at anytime, anywhere, by anyone. To effectively reduce risk, you need to maximize your insight and control of all devices on your network. On average, Forescout customers discover over 25% more connected devices than they knew they had and can collect hundreds more contextual device properties than before. By combining Forescout’s complete enterprise-wide device visibility, rich contextual device and network properties data and automated incident response capabilities with Splunk’s data correlation, analytics and incident management, security operations teams can dramatically reduce risk and increase operational efficiency by realizing numerous benefits
Features and Benefits
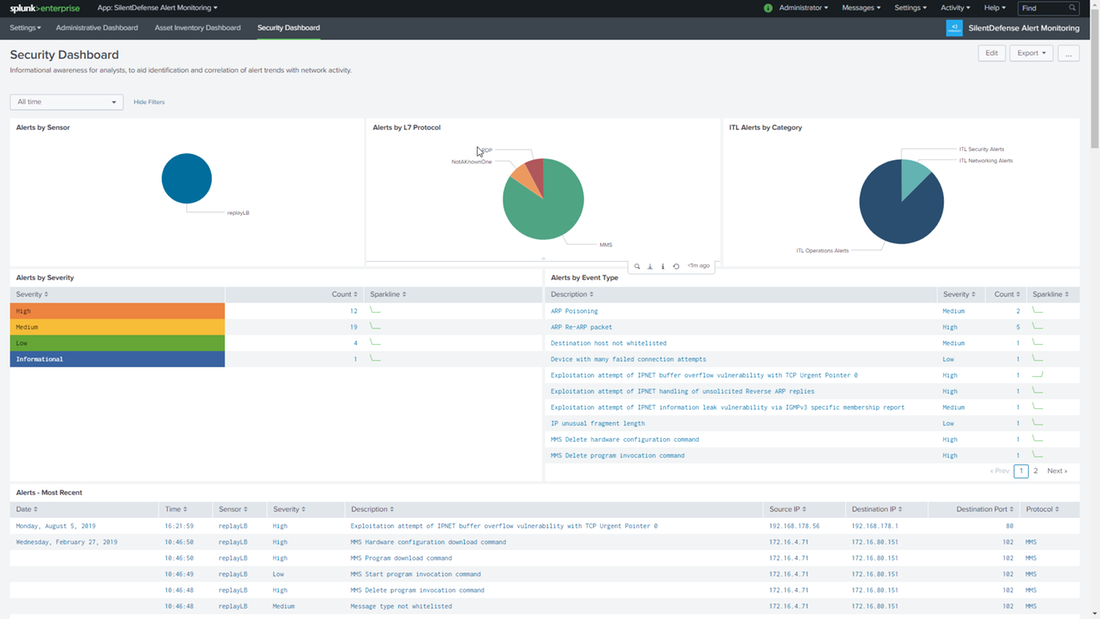
Rapid anomaly detection and accurate trend analysis
Forescout discovers, classifies and assesses all connected devices; compiles this information in the Splunk CIM format and shares it with Splunk. The additional device information from Forescout includes user information, device type, device configuration, network access patterns over time, network location and security posture. Splunk correlates rich contextual data from Forescout with other data sources and uses this information for long-term storage, swift anomaly detection and accurate trend analysis.

Enhanced incident correlation and prioritization
Splunk correlates rich device context from the Forescout platform with other data sources to better identify and prioritize incidents. When Splunk receives alerts from other data sources about a suspicious activity on a device, it shares the information with Forescout. Forescout provides high-value user, network and device context to Splunk. Splunk leverages this additional insight to determine if a suspicious event is actually malicious or violates policy and escalates or reduces the severity of the event based on the device and user context, such as highly privileged or less trusted users.
Automated closed-loop incident response
Forescout scans all connected devices for indicators of compromise (IOCs) and policy violations in real time when alerted by Splunk. Through Splunk’s Adaptive Operations Framework, Splunk operators can initiate Forescout actions—such as isolating or quarantining potentially compromised or noncompliant endpoints depending on the severity of the violation. Forescout can also dynamically trigger policy-based mitigation and response actions until the deviant device is remediated. Forescout then delivers the results back to Splunk to close the loop. Administrators can view the entire lifecycle and final outcome of the event in the Splunk dashboard.
Additional Information
Support
EyeExtend modules are fully supported by Forescout. Please see support details at https://www.forescout.com/resources/activecare-maintenance-and-support-policy/
- Phone: +1-866-377-8773
- Knowledge Base
Categories
-
App Type
-
Built By
-
Licensing Category
-
Works With
Resources
Splunk on SOC Brain Power & Forescout Visibility
Doug Merritt, CEO of Splunk discusses the value of Forescout device visibility feeding Splunk as the SOC brain translating all data feeds into actionable information that Forescout can automatically respond to with orchestrated workflows.
eyeExtend for Splunk® DataSheet
Download PDFeyeExtend for Splunk Configuration Guide
Download PDFSplunk Solution Brief
Download PDF